
The goal of this publication is to help you in the development of your device with a focus on a very hot topic: Cybersecurity. With the content of this publication, you will be able to understand how Cybersecurity (also called software security) can impact your process of development and the design of your device.
Introduction
For introduction content, refer to the Parts previously published.
Identify Security Risks
Scope of your device: data and communication functionalities
To identify the security risks associated with your device you need to establish early in the design and development process your device communication characteristics:
- The data you store and their location in your system,
- The communication channels you use, their protocols, the data and the command they send or receive.
This will allow you to clearly identify the expected capabilities of your device and then to identify the associated threats and vulnerabilities:
- Pure standalone device. Not connected to any server and exchanging data via standard data storage hardware such as USB sticks or CD-ROM.
- Device within safe network infrastructure. Your device is only connected to the local servers of the clinical center that uses it and can exchange data internally, for example via the use of Pictures Archiving & Communication Systems.
- Device with possible updates from remote servers. The only use of the connection to internet and other servers is for update of the device.
- Device with remote monitoring and maintenance from remote servers. Your system sends non-private data to an external server to perform system monitoring and maintenance.
- Device transferring data to an external server to generate an encrypted centralized database with similar devices.
- Device transferring data to an external server and using this server to perform computation and receive results from those computations.
- Devices that can receive new therapies/prescriptions from a health care professional via a remote server.
Debiotech recommends to:
- Identify, early in the development process, the data and communication characteristics of your system.
- Minimize software weaknesses, Establish software security scoring scheme, perform threat modeling and mitigate your vulnerabilities.
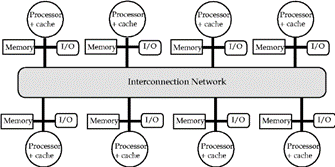
Figure 1. Data, processors and memory location models
Scan for Common Weaknesses Enumeration (CWE)
The CWE is a list of common types of weaknesses that are typically found in software. You can think of it as a dictionary of weaknesses that are found in software. This list is maintained by MITRE, and it is freely accessible.
The most effective method to identify CWEs in your code is to use tools such as Static Application Security Testing Tools (SAST tools). These tools scan the source code just as a static code analysis tool would, but they identify potential security issues instead of potential software bugs (some tools do both). These tools are a great way to identify and prioritize the CWEs in your code.
SAST tools allowing to perform these tasks include but are not limited to:
- Perforce – Klocwork for C, C++, C# and Java,
- Parasoft – Parasoft Test for C, C++, .NET and Java,
- Micro Focus – Fortify which supports multiple operating systems and languages,
- A list of existing tools is maintained by the OWASP (Source Code Analysis Tools | OWASP Foundation)
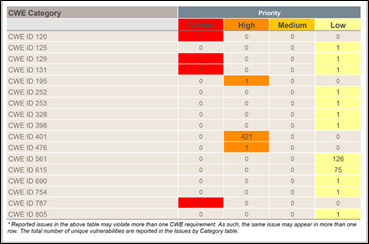
Figure 2. Illustration of Fortify SAST including CWE classification
Debiotech recommends you to:
- Early on in your project execution, start using a SAST tool.
- If possible, make the SAST tool part of your continuous integration environment and define criteria to prioritize the work according to the criticality of the identified weaknesses.
Common Vulnerabilities and Exposures (CVE) identification
This activity is of critical importance for proper software security risk management activities. It consists in the identification of the Common Vulnerabilities and Exposures associated with the third-party libraries and the operating systems you are using. Most of the libraries and software components you integrate within your system provide this information and make it publicly available. However, this information evolves with time. You need to frequently review these vulnerabilities to ensure that your system is protected against recently discovered vulnerabilities. You can do this review manually, but you will quickly benefit from tools allowing you to do this automatically such as Software Composition Analysis tools (SCA tools).
SCA tools allow you to perform the following tasks automatically based on your source code or on your binaries:
- Software Bill Of Materials (SBOM) generation: identification of all the libraries used, their versions and the associated licenses.
- Cybersecurity Bill Of Materials (CBOM) generation: identification of all the Common Vulnerabilities and Exposures associated to your SBOM as for example buffer overflows, SQL injection flaws, Authentication problems, Access control issues and Insecure use of cryptography.
You can then focus on the review of those vulnerabilities, determine if they apply or not to your system and if you must develop a patch to remove them. Please remember that you must provide rationales to argue why you estimate that a vulnerability is not applicable to your system.
SAST tools allowing to perform these tasks include but are not limited to:
- WhiteSource
- Black Duck
- JFrog Xray
- A list of existing tools is maintained by the OWASP (Software Composition Analysis Tools | OWASP foundation)
Debiotech recommends you to:
- Early on in your project execution, integrate within your software development infrastructure an SCA tool for SBOM and CBOM generation.
- Frequently use this SCA tool even if no change is made to your software to stay up to date with latest identified vulnerabilities.
Take the necessary time to identify which vulnerabilities are applicable to your software and provide rationales justifying your position for non-applicable vulnerabilities. For applicable ones, describe the patch you will be developing and the way you will verify its efficacy.
Threat modeling
To identify vulnerabilities of your system, you must apply a threat modeling approach. The first step is to list all the elements that will affect the security of your system:
- Physical ports,
- Internal and external communications mechanisms,
- The list of third-party libraries used by the different communication and authentication mechanisms,
- And more generally all valuable assets of your device.
Then, for each of these elements and assets you need to identify relevant threats. A typical approach for this step consists in using an existing model such as STRIDE or alternatives like LINDDUN or CIA Triad for example. When using STRIDE, for each identified asset, you must evaluate the consequences of:
- Spoofing: The device/service/user is not the one it is supposed to be, like in Man-in-the-Middle attacks,
- Tampering: Illegal access to your device, with hardware or software modifications,
- Repudiation: Claiming to have not performed an action,
- Information disclosure: Expose sensitive information about your device or private data,
- Denial of service: The device does not work as expected,
- Elevation of privilege: Gaining capabilities without authorization.
Finally for each threat, a severity score must be determined (Chapter 6.3.1) to prioritize them.
Dedicated tools exist to help with the threat modeling process, like “Microsoft Threat Modeling tool” or OWASP “Threat Dragon”. These tools will help you to graphically model your system, identify threats using STRIDE and generate a report.
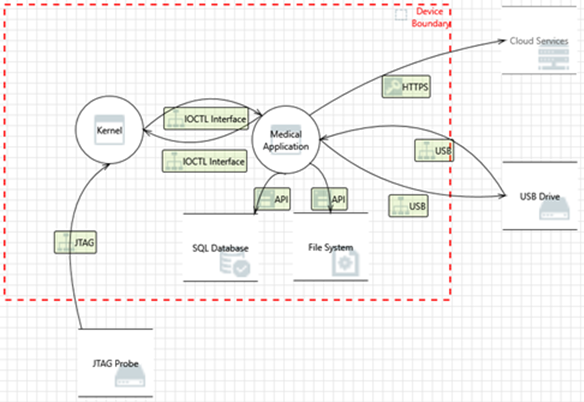
Figure 3. Threat model example using MS Threat Modeling
Debiotech recommends to:
- Follow established threats modelling approach such as STRIDE for example,
- Use threats modelling tools such as MS Threat Modeling to facilitate this work.
Post-market security risk identification
Hackers evolve and improve their technics. The list of known vulnerabilities increases with time and shall be reviewed periodically for your device. New critical vulnerabilities might require developing or integrating a new security patch for your software and distribute it to your users. Depending on the security risk level you may have to react quickly, inform your users about the security risk and provide a solution that can be quickly deployed.
Authors
 |
Rémi Charrier Business Development Director r.charrier@debiotech.com |
||
|
João Budzinski |
 |
||
 |
Laurent Colloud Software Project Manager l.colloud@debiotech.com |
||
|
Gilles Forconi |
 |
Next steps
Debiotech is glad to have the opportunity to share its knowledge with innovative companies from the MedTech industry. Your feedbacks on this publication are welcome and will be used to update it or to create new publications on topics you care about.
Continue your education on medical device development by:
- Accessing Debiotech historic publications: https://www.debiotech.com/news-grid/
- Following Debiotech on LinkedIn to be notified on new publications: https://www.linkedin.com/company/debiotech-sa
- Contacting us to ask a question or request personalized support: contact@debiotech.com
Debiotech would be proud to be your partner and support you with:
- Medical device design & development services:
- Software: Digital Health, Firmware, Embedded, SaMD
- Electronics: Design, Verification and Validation
- Mechanics: Design for micro-fabrication & fluidics systems
- Supply chain development and optimization
- Support in medical innovation management:
- Market analysis and segmentation
- IP management
- Business plan consolidation
- Partnership development


